Data Destruction For Information Security
Why Is Data Destruction So Important?
Large, medium-sized, and even small companies all have something in common; they all produce data one way or another.
Every company is protective of its data, and no one wants their data getting in the wrong hands. Apart from the legal issues that would be involved, there are also security issues and the loss of customers’ trust in the company’s ability to protect their data.
For the sake of data security, customer privacy, and protection of a company’s legacy information, the data stored on hard drives and other memory devices need to be destroyed when such storage devices are no longer in use.

What Is Data Destruction?
Data destruction is the process of completely destroying the data stored on a storage device which could be in the form of a hard disk, tapes, or any other electronic media. The purpose of destroying the data is to ensure that the information cannot be recovered, even with advanced forensic techniques.
Data destruction, however, is not as simple and straightforward as it sounds. While data might no longer be accessible to the operating system and the application that created it, the data may still be reconstructed and recovered by other means.
How Does Hard Drive Destruction Work?
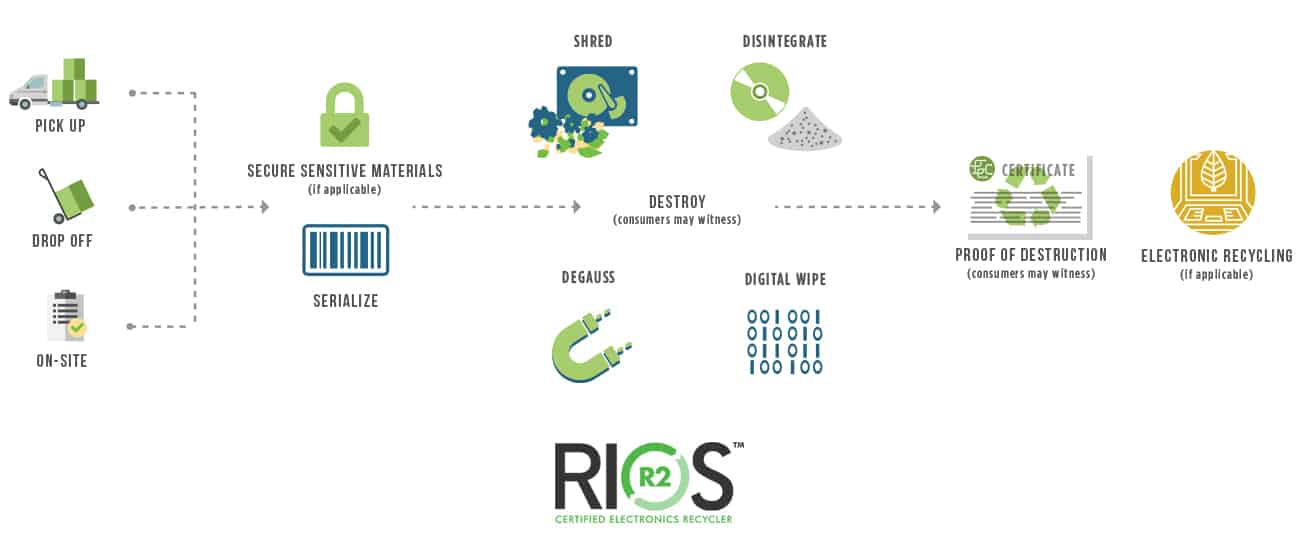
There are various methods available to destroy data and the effectiveness of each method varies.
At its most basic, the process may just consist of deleting the data and overwriting the disk space with new random data. More secure methods involve the physical destruction of the hard drive, possibly by breaking it with tools or drilling it with holes.
An alternative to physical destruction is degaussing. This is a process that uses powerful magnets to create a magnetic field that destroys the data on a device storing large chunks of information.
These are some methods of data destruction:
- Permanent delete / Reformat
- Overwriting data
- Wiping a drive
- Erasure
- Degaussing
- Physical destruction with manual tools like hammer, drill, or crush
- Electronic shredding process
- Solid-state shredding process
Note: The “bolded” data destruction methods are more secure than the ones above them. If the data is very sensitive, then it may be preferable to use a combination of erasure and physical destruction. However, if you need to reuse the storage device, wiping the disk thoroughly might be sufficient.

What Is Hard Drive Shredding?
Hard drive shredding is the process of physically destroying a disk drive, usually with the use of a purpose-built shredder to ensure that the data cannot be recovered. Hard drive shredding can be carried out on-site or taken to a recycling center for processing. Potomac eCycle offers pickup of quantities of drives.
Many people believe that by punching a single hole in their hard drive, they can render the data on the hard drive useless, but this is not the case. However, if hundreds of holes are drilled into the drives at small distances apart, the hard drive can be made completely unreadable—even with advanced techniques.
Professional hard drive destruction companies use powerful hard drive shredders that are capable of shredding a hard drive down to as little as 10mm and compacting it at the same time. Some machines even can disintegrate solid-state drives down to 2mm.
The reason why companies rely more on hard drive shredding is that some bits of data on a hard drive are not destroyed even when they get formatted or overwritten several times. There are several data recovery techniques and advanced forensic software that can recover formatted and even overwritten data.
Whatever method is used to destroy confidential data, it is prudent to obtain a data destruction certificate.
What Is A Data Destruction Certificate?
A data destruction certificate is a document issued by the vendor that performed the destruction to state that the storage media has been thoroughly destroyed and can no longer be regenerated. Potomac eCycle can provide certificates for clients using their data destruction services.
